Two security exploits are currently active for Mac users, including a Parallels Desktop vulnerability. While both are currently rather easy to avoid, knowledge is the best protection against online threats. Below, I explain what’s happening with each threat while sharing how you can best protect yourself.
Vulnerability Found in Parallels Desktop for Mac, Update on the Way
In a new report from MacWorld, two Mac exploits are currently active, one involving the OS emulator Parallels, and the other involving a typical email phishing scam.
Looking at Parallels first, researcher Mickey Jin discussed the issue over seven months ago in an attempt to get a fix from Parallels. This specific vulnerability only impacts Intel-based Macs running the software, in which an attacker may be able to gain root access to the system due to an exploit within the software’s VM creation routine. As MacWorld observes, however, the attacker would first need access to your machine for this attack to be successful.
To address this issue, Parallels is releasing Parallels Desktop 20.2.2 and Parallels Desktop 19.4.2. The update will be issued “within this week”.
Considering Parallels Desktop has automatic updates enabled by default, receiving the update should be incredibly easy. However, you can also check to ensure it’s enabled from the menu bar via the Parallels Desktop icon > Preferences > General >Download updates automatically.
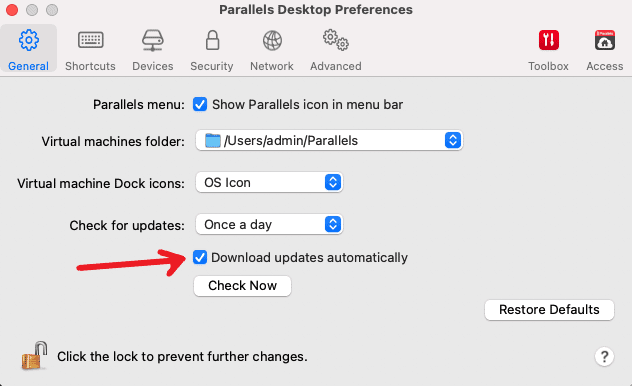
You can also navigate to Parallels Desktop > Check for Updates directly from the menu bar. Along with checking for updates, be aware of who you are allowing to directly access your machine.
FrigidStealer Steals Info . . . Sort Of
The other exploit currently in the wild is pretty easy to avoid. Security firm Proofpoint is the one to thank for discovering this one, and it involves a user receiving a bad-faith email. The email provides a link informing the user they need to update their web browser. Clicking the Update button will save an installer to your system. Opening the installer will provide directions that allow the malware to bypass macOS security system Gatekeeper, giving the malware permission to install itself.
Additionally, those outside of North America are the most likely to receive an attack from FrigidStealer, which steals important files and information involving browser cookies, Apple Notes, and passwords.
Essentially, the best way to avoid this one is by not clicking any suspicious email links. It’s also best to avoid downloading software from anywhere other than the Apple App Store. Of course, one of these things is easier than the other, so remember to stay alert when traversing the great internet landscape.
When it comes to internet security, there’s no such thing as being too careful. Do what you can to protect yourself online, while we here at The Mac Observer will be on the lookout for further security exploits and attacks.
